Security Services
Just as personal hygiene is essential to protect us from virus and germs, cyber hygiene is a quick win to protect an organization from common cyber threats.
Based on numerous reports, such as the one from UK Government’s Communications-Electronics Security Group (CESG), around 80% of cyber-attacks are the result of poor cyber practices within the victim organizations. To address this and minimize the risks of becoming a victim of cyber-attacks, data breaches, or spreading the impact of a cyber-attack to other organization, a cyber hygiene strategy must be implemented.
wizlynx group in Singapore has rolled-out a Cyber Hygiene Assessment service, which is composed of a set of security assessments and follows the Monetary Authority of Singapore (MAS)’s Cyber Hygiene Notice (PSN06) to strengthen Cyber Resilience of Financial Industry.
Taking that into consideration, is your organization and incident response team prepared and ready to fight against any kind of unexpected event?
Our Cyber Hygiene Assessment is highly inspired from various best practice frameworks (MAS Cyber Hygiene Notice, CIS Critical Security Controls, ISO27001, NIST Guides etc.), and focuses on the following areas:
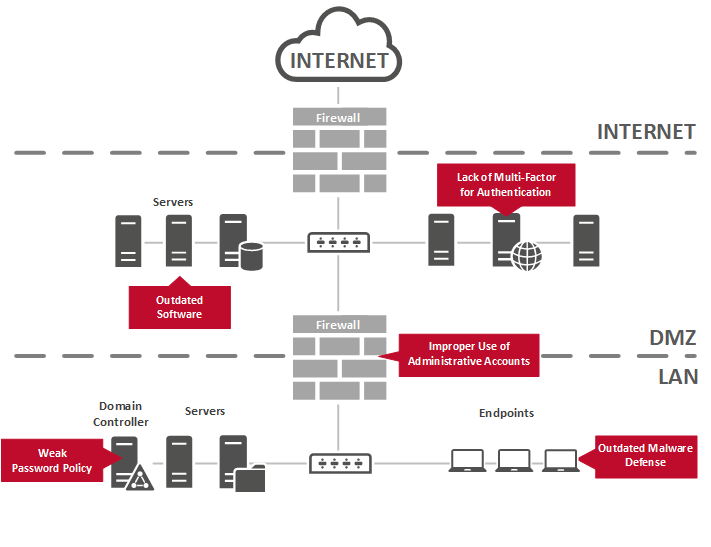
All discoveries of the Cyber Hygiene Assessment will be documented in a final report, where weaknesses will be assessed and supplemented with recommendations and remediation actions, as well as prioritized according to the risk associated. This final report will be discussed during a presentation with you, and will include a comprehensive and meaningful C-level summary of the executed operational technology environment. Additionally, all detailed results with respective evidences and recommendations for future security measures will be fully documented.